Central web server infrastructure
Infrastructure overview
In order for readers to view web pages created by authors using web browsers, several systems must work together.
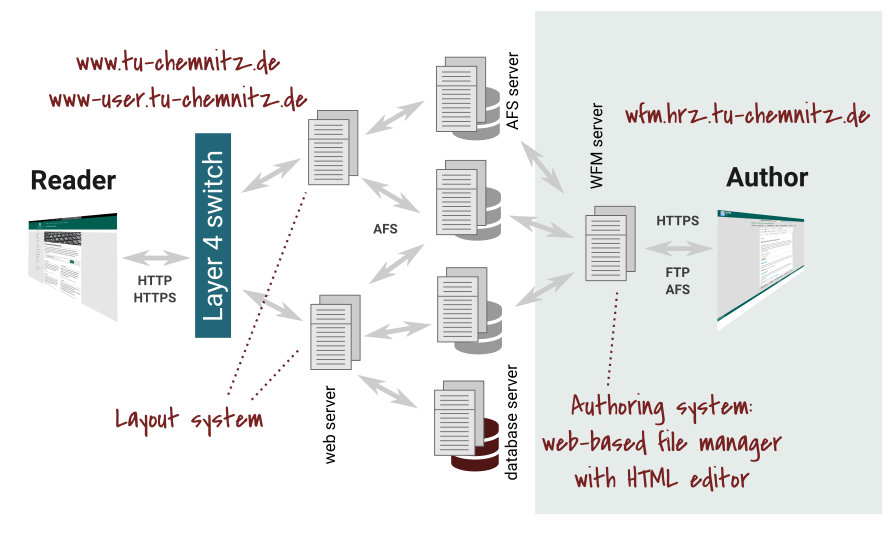
- Layer 4 Switch: reliability, load balancing
- Web server: Linux, Apache, PHP, layout system TUCAL – web server
www.tu-chemnitz.de– central web sites: TU, faculties, divisions, projectswww-user.tu-chemnitz.de– personal homepages of users
- AFS server: data storage = web space
- Database server: MySQL for web applications (PHP, CGI)
- WFM server:
wfm.hrz.tu-chemnitz.de- web-based file manager WFM with authoring system TUCAL
- HTML editor, form to create and edit the "frame"
- Support for the creation of foreign language pages
- Create, rename, delete files
- Set permissions (AFS rights)
- access via SCP, SSH, SFTP also possible
- web-based file manager WFM with authoring system TUCAL
Central web server: services and operation
www.tu-chemnitz.de consists of three Linux servers that appear to the outside world as a redundant system via a level 4 switch. The data (web pages and applications) themselves are also kept on redundant AFS file servers.
The server www-user.tu-chemnitz.de has an analogous structure and serves personal homepages of our users. Other servers fulfil special tasks (e. g. virtual servers for projects).
The special services of the central web servers include:
- Exclusive use of secured transmission via https (Strict Transport Security)
- Use of the script language PHP with database connection (MySQL)
- Individula web pages and PHP applications for users via the web server
www-user.tu-chemnitz.de - Access statistics
- Special services, such as event calendar
- Backup of data (via AFS backup) – Restore of data via webmaster@…
- All features of Apache httpd, documentation for authors
- Advice and support regarding the resolving of problems: webmaster@…
- Contact for security questions also: webmaster@…
Please note:
- As the operator of the central web servers, the URZ ensures their constant maintenance and care (patches, software updates, especially with regard to security).
- However, the URZ cannot guarantee a secure demarcation of web areas and applications.
- A large number of web authors are responsible for the content (web pages). Permissions to post and change content are generally assigned decentrally by those responsible for each department. The URZ cannot make any statement about the sense of responsibility and trustworthiness of the web authors.
- The URZ cannot make any statement about the security of the web programs (PHP, CGI) installed by the web authors. Web authors who install software for web applications are obliged to deal intensively with the functioning of this software and to correct errors or install new versions promptly (especially in the case of security-critical problems).
- To protect the web applications and our servers, it is not possible to establish network connections on the central web servers with computers outside the TU Chemnitz.
- For web applications with increased security requirements, the URZ offers the operation of own virtual servers.
See also:
The central web servers of the TU Chemnitz are operated with open source software: Linux, Apache httpd, PHP, etc.
Acknowledgements
We would like to thank these people for identifying and helping to correct safety deficiencies:
- Secuninja
- Geek_Pwn
- AndresERiveraB
- gopalsingh
- Chriss
- deb_security
- k0t
- Alexis Laborier
- Ezio Paglia
- khan janny
- lacroute serge
- Pethuraj M
- Asim Sattar
- Mughiwara
- Pasan Lamahewa
- warbid
- MrRain_1996
- Harshal S. Sharma / Harshal S. Sharma
- Andrew Hess (any1)
- Foysal Ahmed Fahim
- Mayank Mukhi
- Tanzil Khan
- s41n1k
- khadir osama khadir
- Kasper Karlsson, Omegapoint
- Felipe Gabriel Renzi
- Hitesh Verma
- Ankur Vaidya / 4n_curze
- Nitya Nand Jha(Shunux) / Nitya Nand Jha(Shunux)
- Parth Narula
- Vaibhav Jain
- Adrian Tirado Garcia
- Kishan Shah
- Noob Hunter
- Takshal Patel (tojojo)
Web space: storage for web documents and web applications
- Central web sites of the TU Chemnitz: www.tu-chemnitz.de
- Personal homepages of users: www-user.tu-chemnitz.de
- Own virtual servers
- Virtual web servers
The web space for the central web servers of the TU Chemnitz, i.e. the storage space for web documents and scripts, is located in the AFS file system. Web authors can access it via different ways:
- Web-based file manager WFM:
- with TUCAL – authoring system for creation and maintenance for websites in corporate design
- Assignment of authorizations (AFS rights)
- PCs with AFS clients (computer pools operated by the URZ and administered workstation systems):
- Linux:
/afs/tu-chemnitz.de/... - Windows: network drive U: or H:
- Linux:
- SCP, SFTP:
- Server:
login.tu-chemnitz.de, Directory:/afs/tu-chemnitz.de/...
- Server:
You must always authenticate yourself with your personal login ID. Access is only granted if authorization is available.
Central web sites of the TU Chemnitz: www.tu-chemnitz.de
This server provides interested parties with information about the TU Chemnitz and serves students and staff in their daily work. For web applications, computationally intensive operations, experiments as well as for project handling with external partners please use dedicated web servers (see below).
The data for the central web pages are located in the AFS file system at /afs/tu-chemnitz.de/www/root. All faculties and departments have web space there. Permissions for subdirectories for professorships and projects are assigned by the responsible persons of the areas. Access for authors is possible e. g. via WFM (TUCAL).
For cross-faculty projects or websites that cannot be assigned otherwise, please contact us: webmaster@….
| Directory in file system: | AFS: /afs/tu-chemnitz.de/www/root/urz/www/server.htmlWindows: U:\www\root\urz\www\server.html |
| Access via WWW: | https://www.tu-chemnitz.de/urz/www/server.html |
Personal homepages of users: www-user.tu-chemnitz.de
Students and employees of TU Chemnitz can publish personal websites New: You have to activate your personal website in the security center in your IdM portal – see blog article "Neue Maßnahmen zum Schutz Ihres URZ-Accounts" (protection measures for your URZ account).
The web space is located in the home directory in the directory public_html.
The data in this folder will be available worldwide via
https://www-user.tu-chemnitz.de/~LoginID/, unless you restrict access
(access control). Access for authors is possible e. g. via
WFM.
Required AFS access rights: ip:www-user rl
(see AFS rights).
| Directory in file system: | AFS: /afs/tu-chemnitz.de/home/urz/o/otto/public_html/page.htmlWindows: H:\public_html\page.html |
| Access via WWW: | https://www-user.tu-chemnitz.de/~otto/page.html |
Own virtual servers
When a virtual server is ordered with option
“Webserver aktivieren”, separate web space and special administrator access are provided on an own server.
The name of the server may – but must not – be www.projectname.tu-chemnitz.de – it will be coordinated
with the Press Office and Crossmedia Communications team.
This variante is recommended for increased security requirements (Web Trust Center authentication, …).
Own domain names are also possible.
Virtual web servers
For special web offers via a virtual web server, order a project directory. To set up this server please contact us by e-mail. The name of the server will be coordinated with the Press Office and Crossmedia Communications team, external domains are also possible.
Required AFS access rights: ip:www-virtual rl (see AFS rights).
These web servers are addressable with https (Strict Transport Security, TLS 1.2 or higher, http leads to redirection to https).
Note: Authentication via the Web Trust Center is not possible for virtual servers.


