Cybersecurity and anomaly detection
The wide spread of computer systems in modern industry, economy, and our daily life help to improve productivity, increase efficiency, and manage a world that gets more and more complex. Despite these benefits, the successful usage of a computer system depends on two aspects: First, it must be protected against cyber attacks from inside and outside the system. Second, to guarantee faultless processing of the system, the computer system must be monitored to detect problems and anomalous system behavior early enough. Especially in these modern times, where cyber-attacks increase it is important to minimize faulty processing in cyber-physical systems, industrial control systems, or in the area of critical infrastructure.
We study how different deep-learning methods can be used to monitor relevant computer systems. Due to the variety of data and information (e.g. sensor data in a tabular format, network traffic in byte format, or log data containing words and numbers), different methods from autoencoders to transformers must be considered and evaluated. Due to the fact, that in computer systems a high amount of data can be created in a short amount of time, most datasets did not provide labels. As a consequence, mainly self-supervised and unsupervised methods are the focus of our research.
The aim of the WAIKIKI ("Wissensbasierte Anomalieerkennung mittels Kuenstlicher Intelligenz in Kritischen Infrastrukturen") project is to detect cyber-security-related anomalies in critical infrastructure. To realize this, we cooperate with researchers from the professorship of IT security (Prof. Dr. Andriy Panchenko) at the Brandenburgisch Technischen Universitaet Cottbus-Senftenberg and four partners from the industry.
The detection will be realized by the parallel monitoring and analyzing of network traffic and log data. For the latter, we use a compact convolutional transformer (CCT) (proposed by Hassani et al. (2021)) to detect anomalies in log data. It has been shown that transformers are able to encode the context in which a word appears. Due to this, we assume the analysis of log lines is a natural language task.
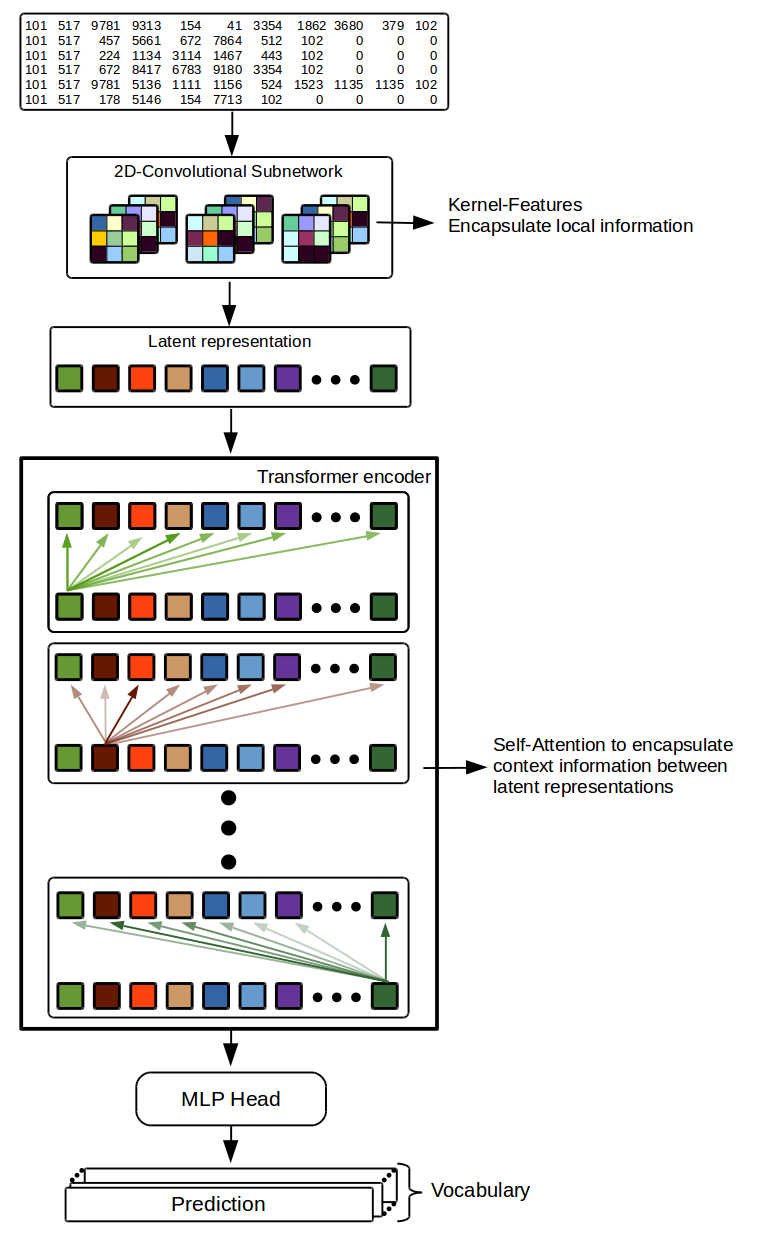
The CCT allows the process of multiple consecutive log lines at once and provides more contextual information to learn the correct system status. If a wrong log notice is detected, which does not fits in the actual context (for example a wrong process number or an error), this can be detected by the network.
Associated projects
BMBF project WAIKIKI "Wissensbasierte Anomalieerkennung mittels Kuenstlicher Intelligenz in Kritischen Infrastrukturen". 16KIS1199 (2019-2023)
Selected Publications
Larisch, R., Vitay, J., Hamker, F. H. (2023)
Detecting Anomalies in System Logs With a Compact Convolutional Transformer
IEEE Access, Volume 11. doi:10.1109/ACCESS.2023.3323252.
Read Article